Automatically remove Intune devices from a group after a wipe
I am sitting here under the Tuscan ☀️ and this blog post had been waiting to be published for a long time. And not just any blog post, but one in which I delved into the wonderful world of Logic Apps and the Graph API.
So why would you think?
Well, I got a question from a customer about whether it was possible to automatically pull laptops out of an exception group after a wipe action was performed in Intune.
Unfortunately, I could not find anything in terms of a blog post or any other form of information, so I just sat down for it.
Fortunately, I had Peter Klapwijk as a supporter who occasionally helped me with certain Logic App settings.
What we need:
- Azure subscription
- Managed Identity
- Intune Audit Logs
- Logic Apps
Let's get to work.
Azure Subscription
Of course, you need an Azure Subscription to be able to configure a Logic App.
If you don't have an Azure Subscription yet, you can create a Pay-As-You-Go Subscription. This means you link your credit card to it and then your Azure usage will be debited monthly.
My Logic App runs every minute and costs about €1-€2 per month. So that is manageable. For the money you do not have to let it go.
Managed Identity
Logic Apps uses a Managed Identity, and you give this account a few minimal API rights so that Logic Apps can retrieve its information from the Graph API and perform certain actions.
How do we create a Managed Identity?
- Go to the Azure portal and sign in
- Click on "Create a resource" and search for "Managed Identity" and click on "Create" again
- Select your Subscription, Resource Group, and Region, and finally give the MI a name
- Click on "Review + Create"
- Click on "Create"
Your newly created Managed Identity can be found under "Enterprise Applications" and then filtered on "Managed Identities".
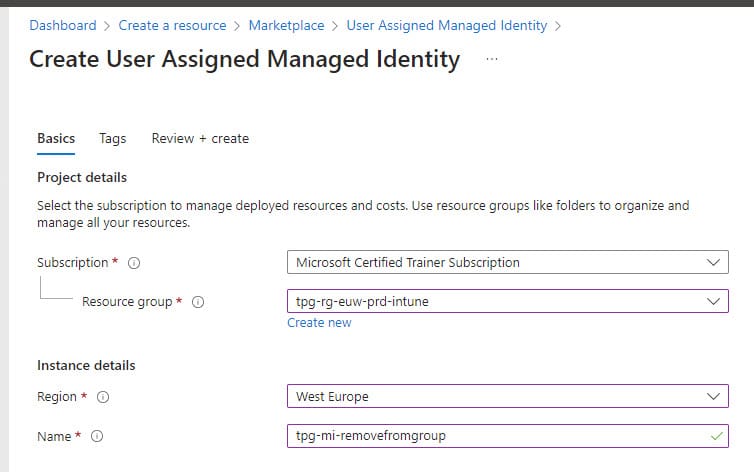
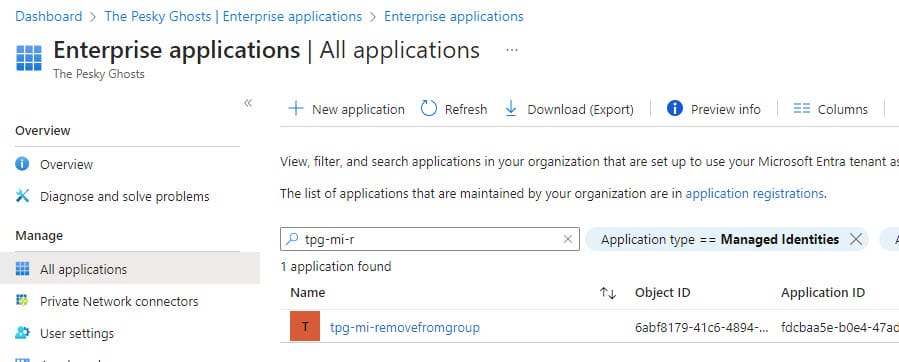
Figure 01 & 02 - Create Managed Identity and find it as an Enterprise Application
API permissions
We now have an MI, but without permissions, it is useless to us, so we need to go and set the following permissions using Powershell.
The rights required by the MI are:
DeviceManagementManagedDevices.Read.All
Device.Read.All
Group.ReadWrite.All
Directory.Read.All
GroupMember.ReadWrite.All
To execute this, we need the following Powershell script to execute.
Install-Module Microsoft.Graph -Force -AllowClobber
Connect-MgGraph -Scopes Application.Read.All, AppRoleAssignment.ReadWrite.All
$MId = "object-id of MI"
$roleNames = "DeviceManagementManagedDevices.Read.All", "Device.Read.All", "Group.ReadWrite.All", "Directory.Read.All", "GroupMember.ReadWrite.All"
$getPerms = (Get-MgServicePrincipal -Filter "AppId eq '00000003-0000-0000-c000-000000000000'").approles | Where-Object Value -in $roleNames
foreach ($perm in $getPerms) {
New-MgServicePrincipalAppRoleAssignment -ServicePrincipalId $MID -PrincipalId $MID -ResourceId (Get-MgServicePrincipal -Filter "AppId eq '00000003-0000-0000-c000-000000000000'").id -AppRoleId $perm.id
}
Disconnect-MgGraph
$MId is the Object ID of the MI
$roleNames are the roles listed above.
Intune Audit Logs
For every action you do in Intune, an audit log is written. So, if you do a sync manually and, in this case, also a wipe action. But the rest of the device actions are also audited.
Here, we do not need a Log Analytics Workspace. Because we will soon be calling these device actions via the Graph API.
The device actions can be found in Intune, under Device -> Monitor -> Device Actions.
Logic App
We now have an MI with the proper privileges, and we have the Intune Device Actions audit logs. Now we are going to make sure that we can use both of them to create an automatic process.
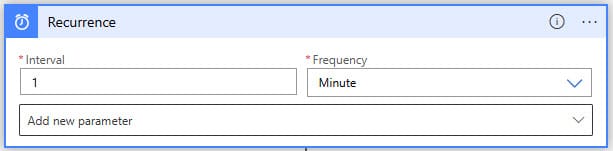
Recurrence
We start with a 1-minute Recurrence that this flow should run.
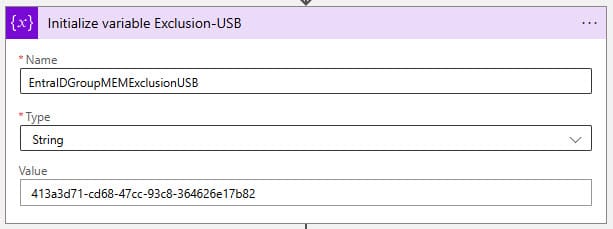
Initialize variable Exclusion-USB
The variable we give here is the Object ID of the exclusion group.
HTTP Get RemoteActionAudits
In this step, we're going to call the Graph API, using the following URI:
https://graph.microsoft.com/beta/deviceManagement/remoteActionAudits?$filter=requestDateTime%20ge%20{formatDateTime}%20and%20action%20eq%20'factoryReset'
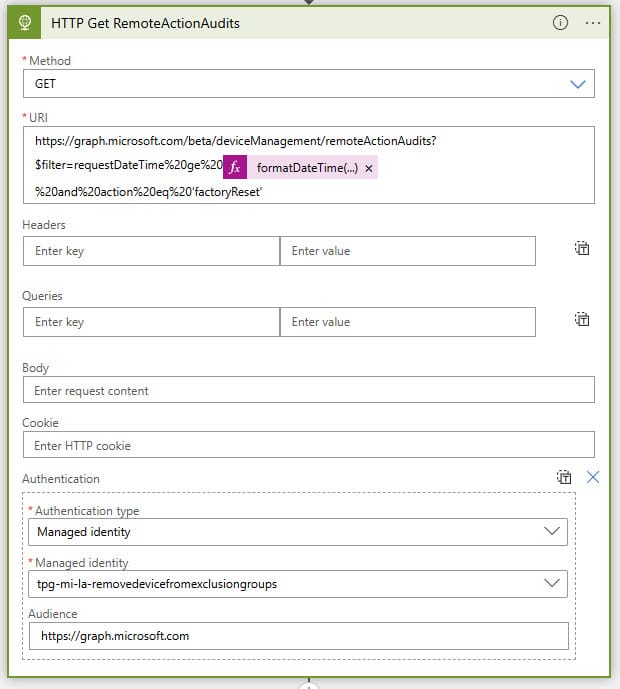
{formatDateTime} has the following expression:
formatDateTime(addMinutes(utcNow(),-5),'yyyy-MM-ddTHH:mm:ss.fffffffK')
For Authentication Type, we choose Managed Identity and then choose the MI account we created.
In Audience, you type https://graph.microsoft.com
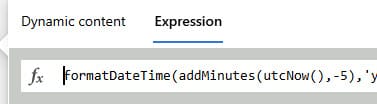
Parse JSON Get RemoteActionAudits
In this step, we make sure that the Graph API request can be converted into a JSON, so that we can use this data again in the next step.
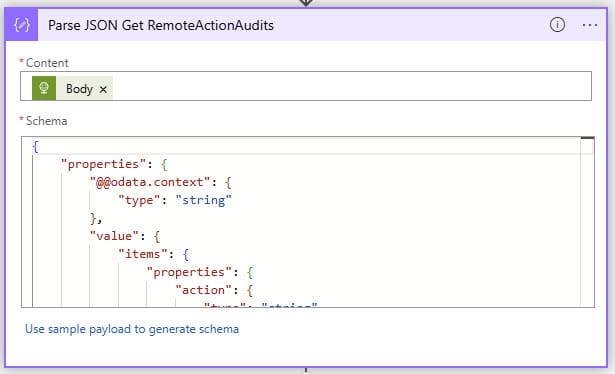
The first part is ready. Now comes the hardest part.
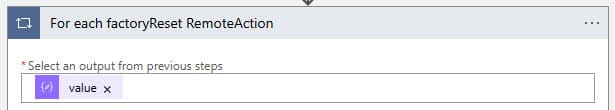
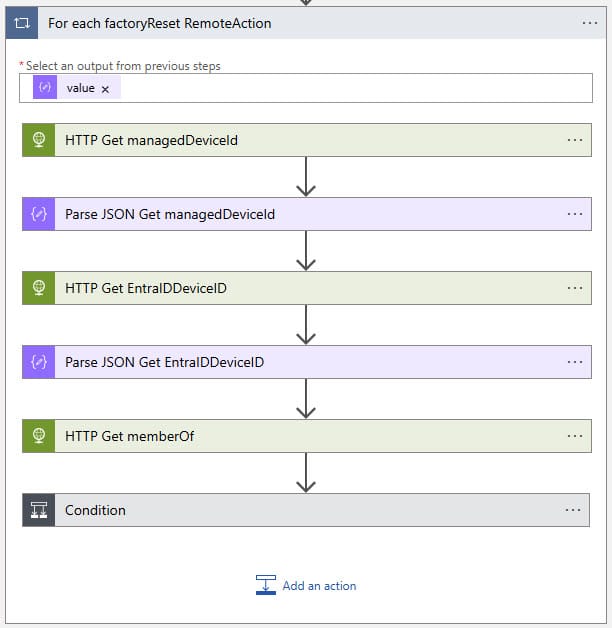
For each factoryReset RemoteAction
Here we choose the value of the previous step as the output of the previous steps.
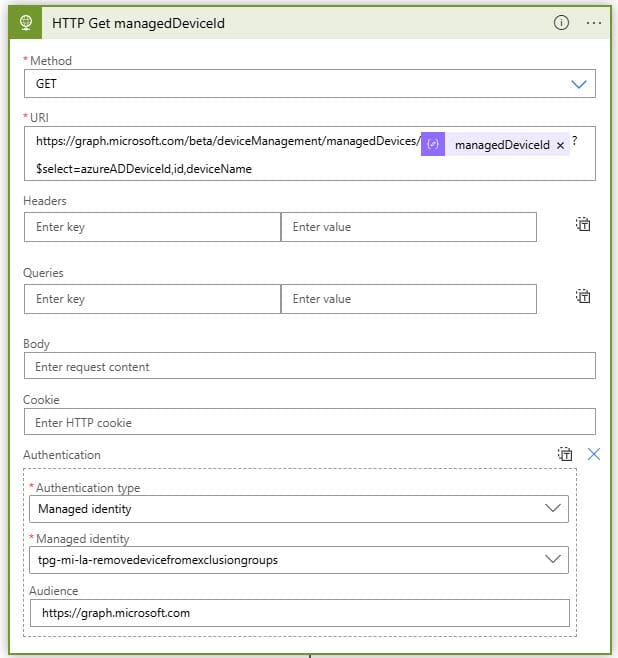
HTTP Get managedDeviceId
Now we ask for the managed device, the Entra ID device object, via the Graph URI
https://graph.microsoft.com/beta/deviceManagement/managedDevices{managedDeviceId}?$select=azureADDeviceId,id,deviceName
We also take this step with the Managed Identity that we have created.
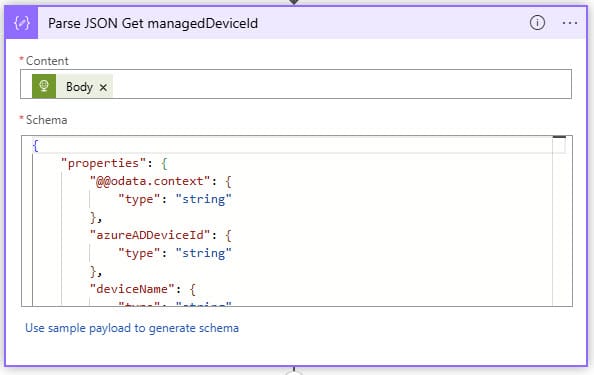
Parse JSON Get managedDeviceId
In this step, we have the output from the previous step poured back into a JSON, so that we can use this information again as well.
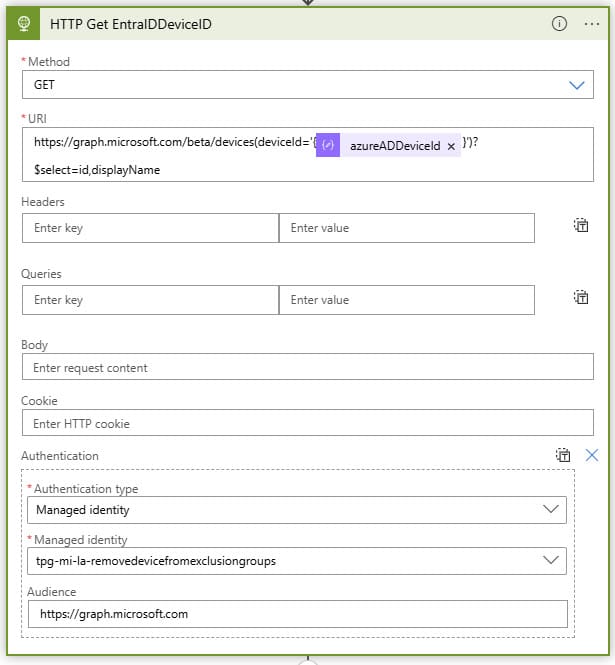
HTTP Get EntraIDDeviceID
In this step, we want to know the Entra ID Object ID of the device. We do this with the URI
https://graph.microsoft.com/beta/devices(deviceId='{azureADDeviceId}')?$select=id,displayName
And we also do this with our Managed Identity account.
Parse JSON Get EntraIDDeviceID
Next, let's pour the output back into a JSON.
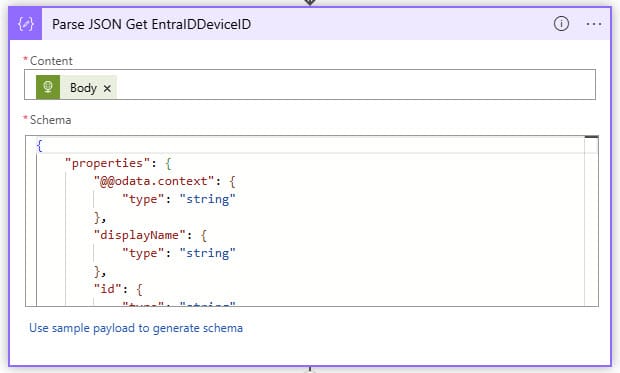
Get memberOf
In this step, we will use the Entra ID Object ID to see if the device is a member of our exclusion group. We do this by using the URI
https://graph.microsoft.com/v1.0/devices{'id'}/memberOf/{'EntraIDGroupMEMExclusionUSB'}
Of course, we do this again with the Managed Identity account.
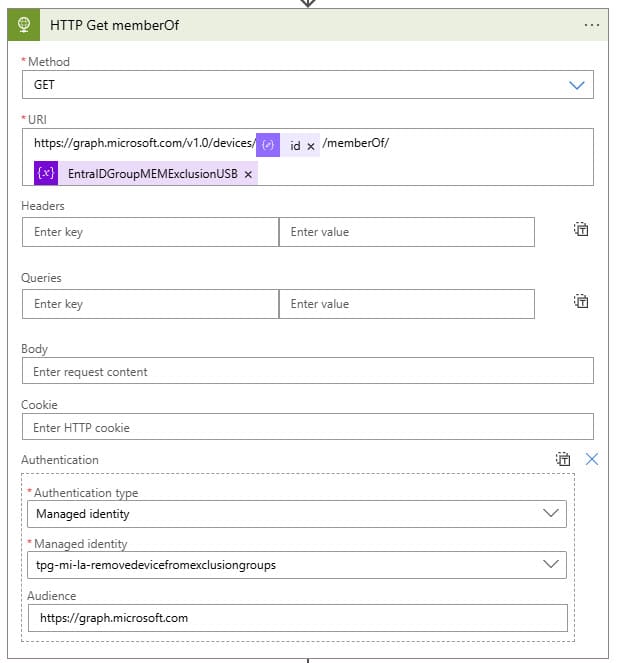
Condition
If the above step returns a status code of 200, which means that the device is a member of our exclusion group, then proceed to True
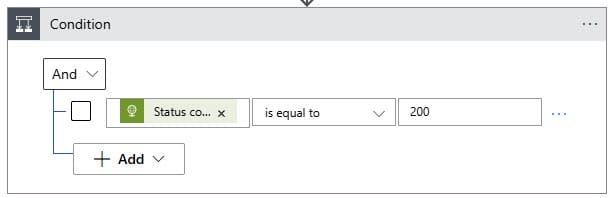
True – HTTP Delete Membership
In this step, we will remove the device, which is a member of the exclusion group, from that group. We do this by choosing DELETE as Method and
https://graph.microsoft.com/v1.0/groups/{'EntraIDGroupMEMExclusionUSB'}/members/{'id'}/$ref
as URI. We also do this through Managed Identity.
False
We leave it empty. We do not do anything with this.
Now the whole flow is ready and we can start testing. This allows you to see if the flow is working in any case and you can remove any errors.
Another test is to make a device a member of the exclusion group and then click on the Wipe button and see what happens.
Fingers crossed.
That is it for now. Until next time. 👋