The BitLocker HAADJ Nightmare
Today a quick blog post about the problem with HAADJ devices and how to turn on BitLocker. Last month I was giving Intune training to 2 different end customers.
During the first training, I was asked if I knew a solution to enable BitLocker on HAADJ devices by means of Intune. Because they ran into problems with the message that the recovery key cannot be backed up to (Azure) Active Directory. Unfortunately, I don't have a screenshot of that anymore.
With this solution in mind, I was able to give this solution to the second end customer immediately and they could test it immediately. And it worked and was immediately satisfied.
But at least here is the solution to enable BitLocker on HAADJ devices by means of an Endpoint Security Encryption policy and, yes, also, a GPO with some basic settings.
I assume you already have a fully configured Intune BitLocker policy. Below you will find the necessary BitLocker settings for a GPO.
- Go to Computer Configuration -> Administrative Templates -> Windows Components -> BitLocker Drive Encryption
And configure the following settings:
-
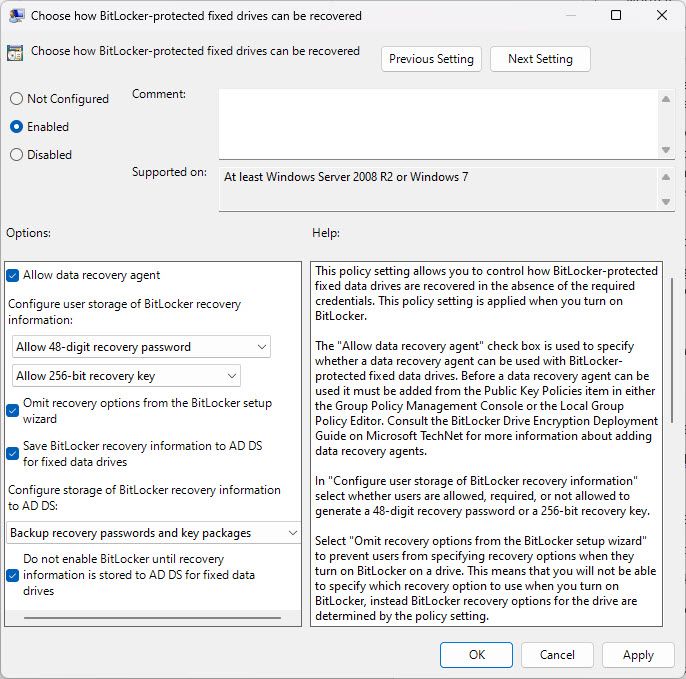
Fixed Data Drives -> Choose how BitLocker-protected fixed drives can be recovered -> Allow 48-digit recovery password and Allow 256-bit recovery key
-
Tick Omit recovery options from the BitLocker setup wizard
-
Tick Save BitLocker recovery information to AD DS for fixed data drives
-
Select Backup recovery passwords and key packages
-
Tick Do not enable BitLocker until recovery information is stored to AD DS for fixed data drives
-
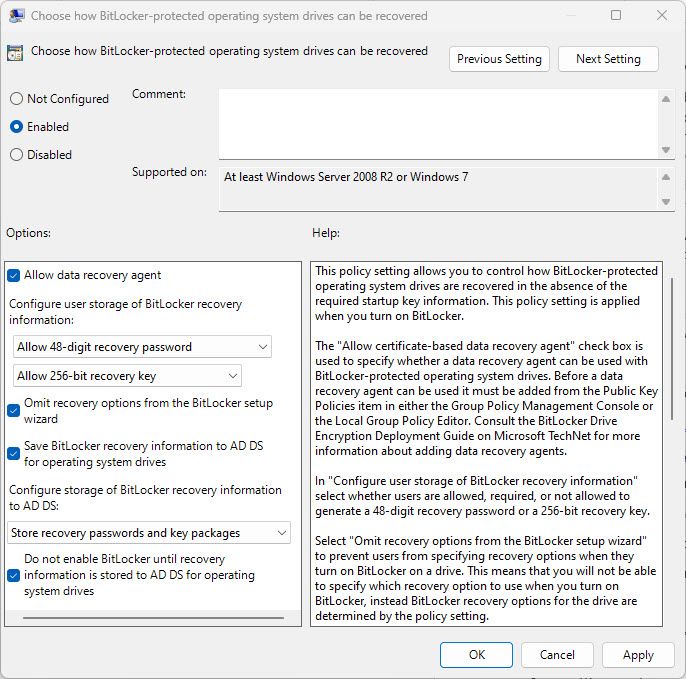
Operating System Drives -> Choose how BitLocker-protected operating system drives can be recovered -> Allow 48-digit recovery password and Allow 256-bit recovery key
-
Tick Omit recovery options from the BitLocker setup wizard
-
Tick Save BitLocker recovery information to AD DS for operating system drives
-
Select Backup recovery passwords and key packages
-
Tick Do not enable BitLocker until recovery information is stored to AD DS for operating data drives
-
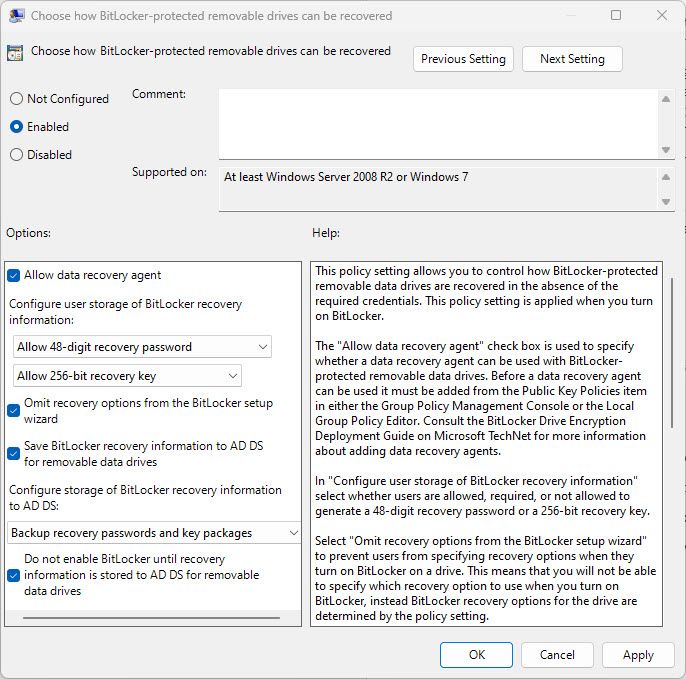
Removable Data Drives -> Choose how BitLocker-protected removable drives can be recovered -> Allow 48-digit recovery password and Allow 256-bit recovery key
-
Tick Omit recovery options from the BitLocker setup wizard
-
Tick Save BitLocker recovery information to AD DS for removable data drives
-
Select Backup recovery passwords and key packages
-
Tick Do not enable BitLocker until recovery information is stored to AD DS for removalble data drives
I hope this is of valuable information to anyone who is fiddling with this.
Until next time.