Setup a Break the Glass account and get alerts (Part 2/2)
This tutorial is part two of a serie.
Part 1 : Create the account and exclude MFA
Part 2: Configure Microsoft Cloud App Security
In part 1, I described how we create the breaktheglass account and exclude it so, that there will be no MFA prompt when you logon with this account.
Other big thing is to monitor regularly of this account has been used unauthorized in your tenant. You can do that with the default sign-in logs from AzureAD, but this log is max 1 month old.
So I looked further and came across by Microsoft Cloud App Security.
Microsoft Cloud App Security is a multimode Cloud Access Security Broker. Also known as a CASB. It provides better visibility, control and sophisticated analytics to indentify and combat cyberthreats in your tenant. For more information about MCAS, check this website.
With MCAS we can send emails and text messages to Administrators when the breaktheglass account has been used.
In this post, I will explain how you can configure this.
6. Configure MCAS
- Open the MCAS portal at https://portal.cloudappsecurity.com and logon with your Administrator account.
- Go to Policies under the Control section
- Click on Create Policy (the blue button) and click on Access Policy
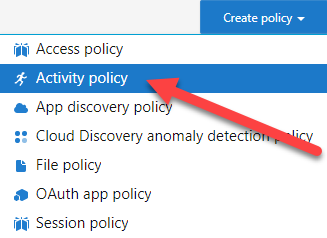
- When the Create Activity Policy window has been opened, just fill it in like the below screenshot. You can set the amount of daily emails to your satisfaction.
- If everything goes well, then you will see something like this
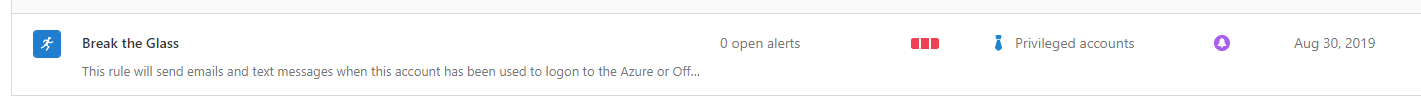
- Now it’s time to test this policy. Open a new (inprivate) browser and log on with the breaktheglass account. After you logged on, you will receive within a few minutes an email and a text message.
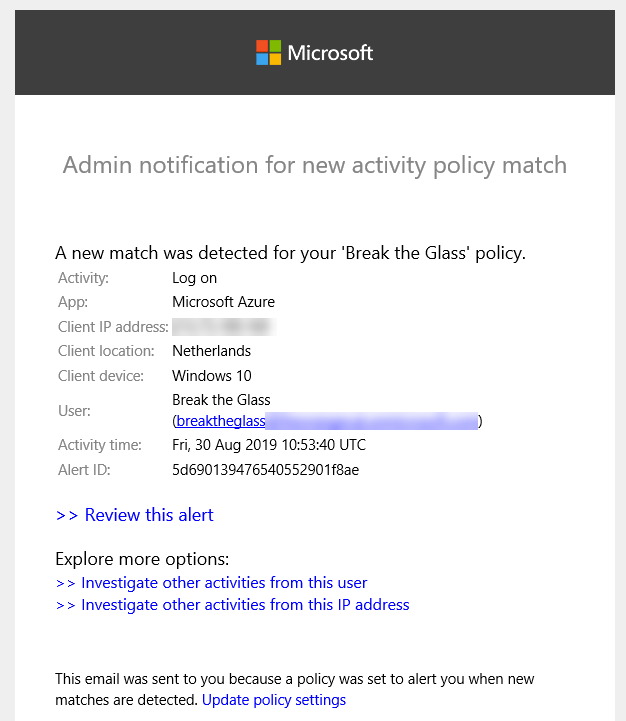
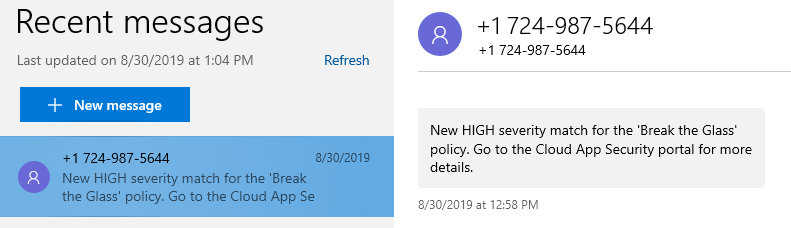
That’s it. I hope you liked this tutorial and good luck with your emergency account.